Phishing Images

Best Practices For Phishing Protection A Guide To Prevent Phishing Scams For Businesses Duocircle

Why Hackers Create Phishing Campaigns

How To Spot A Phishing Email

Phishing Decision Tree Help End Users Identify Suspicious Emails Proofpoint

6 Sure Signs Someone Is Phishing You Besides Email Malwarebytes Labs Malwarebytes Labs

10 Types Of Phishing Attacks And Phishing Scams Hashed Out By The Ssl Store
Apr 15, 19Microsoft Issues Hotmail, MSN And Outlook Phishing Warning (Photo by Jaap Arriens/NurPhoto via Getty Images) Getty Users of Microsoft.

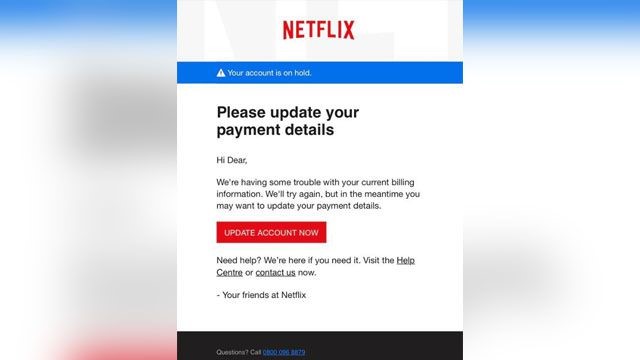
Phishing images. Photograph Getty Images To revist this article, visit a new round of sophisticated phishing attacks is focused on the complex supply chain that will get them to people in need. Oct 08, 19Photo (c) wutwhanfoto Getty Images Just about everyone has a Netflix account these days, and scammers have taken notice They’re using the popular streaming service as bait in a new phishing. Phishing emails will often ask you for personal information in an effort to obtain access to your financial assets and identity Responding with sensitive information (like account numbers, passwords, or Social Security numbers) is never a good idea Did you open any links or images within the suspected email?.
Sep 18, Navigate to a website that offers a thirdparty malware scanning program A malware scanner will scan your computer and detect existing malware, including any malware that may have slipped through undetected by your current antivirus program. Terminology Synonyms include con, confidence game, confidence scheme, ripoff, scam, and stratagemThe perpetrator of a confidence trick (or con trick) is often referred to as a confidence (or con) man, conartist, or a grifterThe shell game dates back at least to Ancient Greece Samuel Thompson (11–1856) was the original confidence man Thompson was a clumsy swindler who. IRONSCALES is a comprehensive selflearning email security platform for both security teams and employees, designed to quickly detect nefarious emails slipping through traditional antiphishing defenses, responding to them automatically in seconds, blocking them for good.
Jan 15, 21Phishing emails – especially when impersonating popular brands – contain widely known brand logos and other images to give the illusion of having been sent by legitimate organizations. Dec 03, A refrigerated truck drives out of the Pfizer Manufacturing plant in Puurs, Belgium, on Thursday, Dec 3, British officials on Wednesday authorized a COVID19 vaccine for emergency use, greenlighting the world's first shot against the virus that's backed by rigorous science and taking a major step toward eventually ending the pandemic. Criminals behind a recent phishing scam had assembled all the important pieces Malware that bypassed antivirus—check An email template that got around Microsoft Office 365 Advanced Threat.
Covid19 vaccine phishing scam circulating in North Text message tells recipients they are ‘eligible’ for jab and seeks bank details Thu, Jan 7, 21, 1746. Jan 17, 19(Note Gmail and some other services prefetch images to avoid this problem) Also bear in mind that spam and phishing emails may include attempts to infect your computer with malware. Phishing is a type of online identity theft Scammers use messages designed to look as if they are from a genuine company to try and trick you into giving out private information like your BT ID username and password or even your bank details.
Bing Help Bing Help See a list of Bing Help topics Popular topics. Phishing scams always involve getting an unsuspecting individual to click on a link or file sent in an email that will download dangerous malware onto their computer If you get an unsolicited email and you aren’t sure who it really came from, never click on any links, files, or images it. Did you enter or submit your.
Jan 22, 21Example of a phishing email and misleading website Image showing an example of a scam email with a document attachment confirming a claim form has been submitted.

How To Stop Phishing Emails Consolidated Technologies Inc

What Is A Phishing Email 5 Examples Of Phishing Emails And How To Avoid Them

Phishing Vishing Smishing What You Need To Know Cyberscout

What Are The Latest Phishing Scams To Watch For In Technology Visionaries Llc

How To Avoid Phishing Terranova Security

Phishing Everything You Need To Know Spanning Cloud Apps

Protection Against Phishing Adp

What Is A Phishing Attack Phishing Email Examples

What Is Phishing Examples And Phishing Quiz Cisco

Phishing Protection Checklist How To Protect Yourself From Phishing
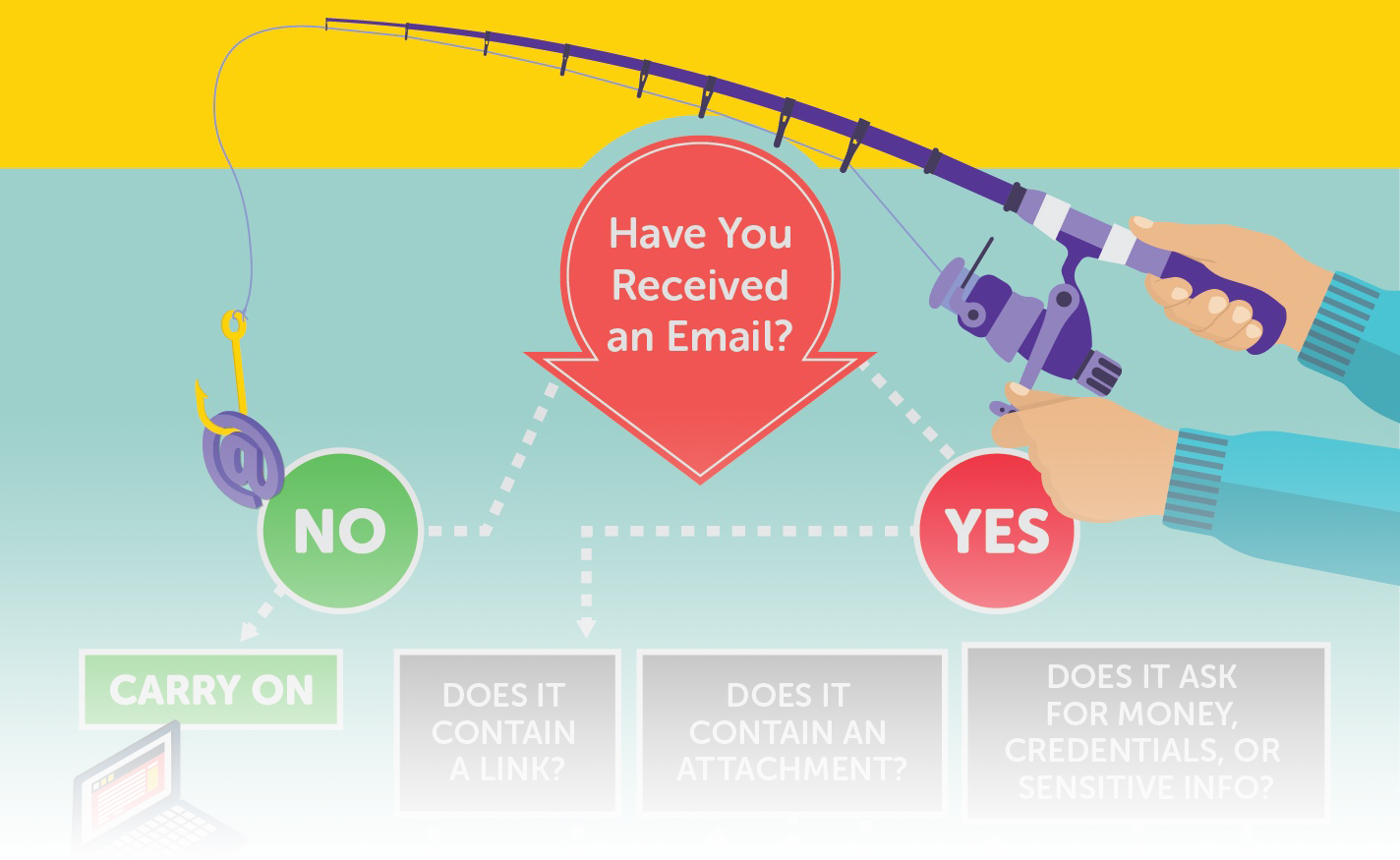
Avoiding Phishing Emails

1 Phish 2 Phish Tips To Avoid A Phishing Email Scam Simply Smart Insights

5 Ways To Spot A Phishing Email Stay Safe Online

Phishing Attacks A Guide To Cyber Security Gaspar Insurance Services

How To Prevent Detect And Protect Yourself From Phishing Attacks

Spear Phishing Next Gen Endpoint Detection And Response

Phishing Attacks Target Workers Returning To The Office Techrepublic

Penn State Community Reminded To Be On Alert For Phishing Email Scams Penn State University

What Is Phishing A Brief Guide To Recognizing And Thwarting Phishing Attacks Cybersecurity Comptia
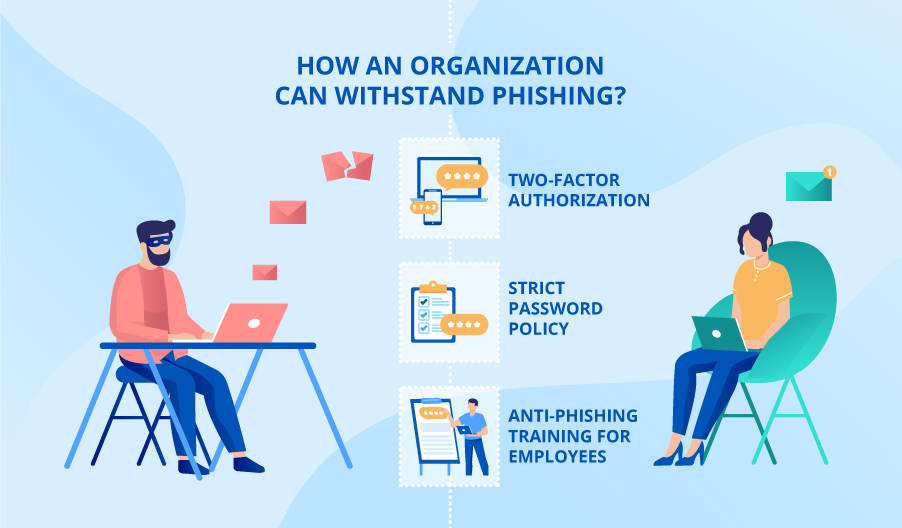
How To Prevent Phishing Attacks On Your Company Real Life Examples And Tips

Must Know Phishing Statistics Updated 21 Tessian

Phishing Goes Viral Covid 19 Themes In Cybercrime

This Google Quiz Tests If You Can Spot Email Phishing Scams

Strangest Phishing Lures Of 19 From Divorce Papers To Real Estate Decoys Threatpost

How A Password Manager Protects You From Phishing Scams

Knowbe4 Releases The Top Clicked Phishing Emails For Q1 Cyber Florida
Q Tbn And9gcqe5de6q13x7whlv3 My Lr1 Dyljkyve7hmmqdm5jrtdsi0rj Usqp Cau

What Is A Phishing Attack Definition And Types Cisco

Phishing Statistics 19 The Shocking Truth Comtact

10 Tips To Protect Yourself From Phishing Kaspersky Official Blog

Phishing Scheme Uses Google Drive To Avoid Security Report

How Phishing Works And How To Avoid It Inc Com

What Is Phishing Everything You Need To Know To Protect Yourself From Scam Emails And More Zdnet
Phishing What Is Phishing

Phishing Education University It

How Phishing Emails Try To Trick You Privacy Policies

What Is Phishing Detect Prevent Phishing Emails Avast

Twitter Spear Phishing Attack Highlights Security Weaknesses Of Social Media

What Is Phishing And How To Recognize It Mailjet

Phishing Cybersecurity Unlv Information Technology

This Phishing Email Scam Cost 2 3 Million My Techdecisions
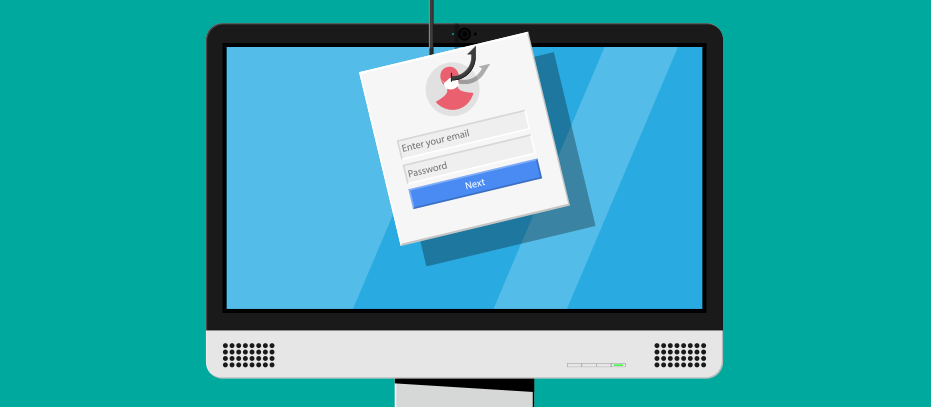
5 Signs Of A Phishing Email During The Covid 19 Pandemic Delta Risk

Phishing 101 What You Need To Know

9 Top Anti Phishing Tools And Services Cso Online
3

Top 6 Phishing Trends Of

How To Spot Phishing The Most Common Cyberattack By Jigsaw Jigsaw Medium
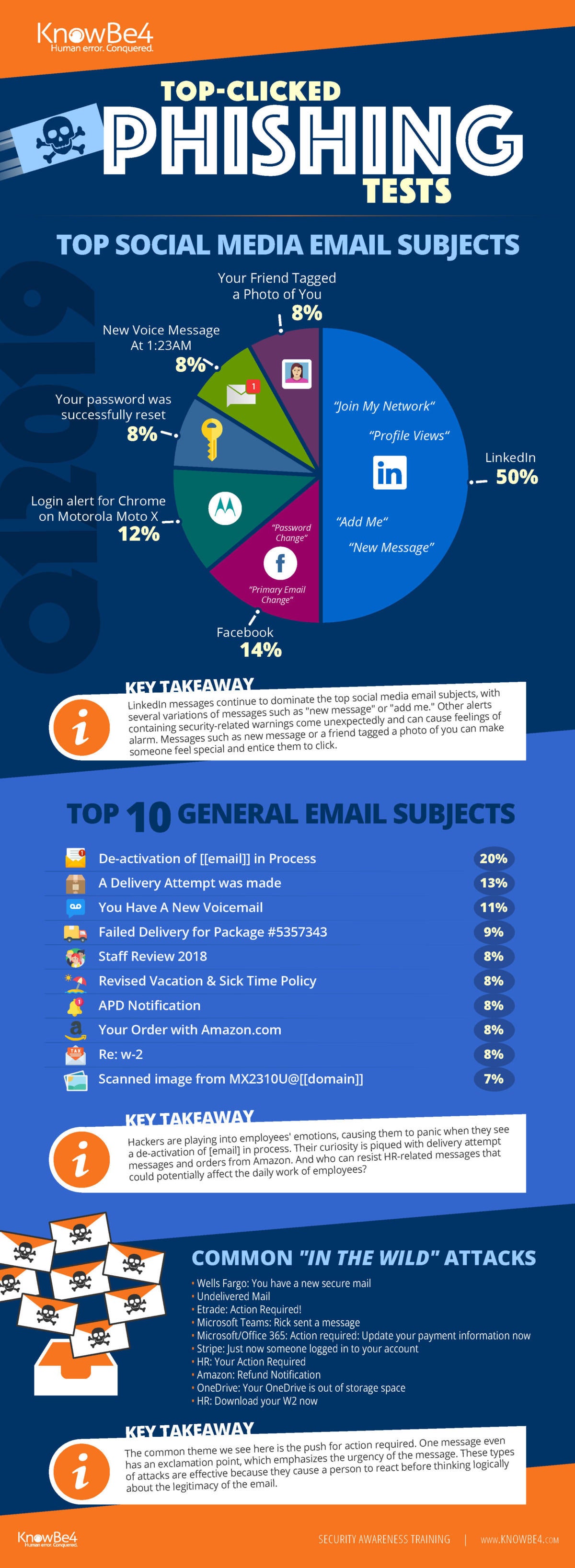
What Is Phishing How This Cyber Attack Works And How To Prevent It Cso Online

Covid 19 Related Phishing Attacks Grew By 600 Worldwide

It News Phishing At The U New Scam To Look Out For University Of Miami Information Technology

How To Identify Phishing Emails And Spare Your Pc Hp Tech Takes
Q Tbn And9gctreghykodxajjvry1onavjqxygjmjdc0mtmez 4i4 Usqp Cau

What Is A Phishing Kit And How To Spot One Zerofox

How To Avoid Phishing Scams Pcmag

Instagram Clamps Down On Fake Messages With Anti Phishing Tool Malwarebytes Labs Malwarebytes Labs
How To Recognize And Avoid Phishing Scams Ftc Consumer Information

Phishing Drill Prepares Community For Email Scams Duke Today

Europol Spear Phishing The Most Prevalent Cyber Threat Affecting Orgs Across The Eu Help Net Security

What Can Organisations Do To Prevent The Rise Of Phishing Attacks Intelligent Cio Africa

How To Spot A Phishing Scam

What Is Spear Phishing Definition And Risks Kaspersky

Over Half Of Organizations Were Successfully Phished In 19 Help Net Security

Beware Phishing Attacks Are On The Rise Pcmag

Google Wants To Quiz You On Phishing Emails The Verge

What Is Phishing How To Protect From Types Of Phishing Malwarebytes
Email Phishing Vishing Other Types Of Attacks Webroot

What Is Phishing Nordvpn

3 Reasons Why There Has Been A Rise In Phishing

Common Phishing Scams And How To Recognize And Avoid Them
Q Tbn And9gcts2jx3esttjk8pntxsukkyvbkpikq7pfncm Dvqrrbsqymhml3 Usqp Cau

Why We Fall For Phishing Emails And How We Can Protect Ourselves

Re Hashed Phishing Email Examples The Best Worst Hashed Out By The Ssl Store
What Is Phishing And How Can You Protect Your Business 1password

Free Phishing Test Take The Quiz To Test Yourself

Phishing Scams Are Becoming Ever More Sophisticated And Firms Are Struggling To Keep Up

4 Phishing Attack Trends Of 19 Id Agent

Phishing Vishing And Smishing What Are They And How Can You Protect Yourself va

Coronavirus Fears Lead To New Wave Of Phishing Malware

Spear Phishing Vs Phishing Terranova Security

10 Top Tips To Detect Phishing Scams Blog Securityhq
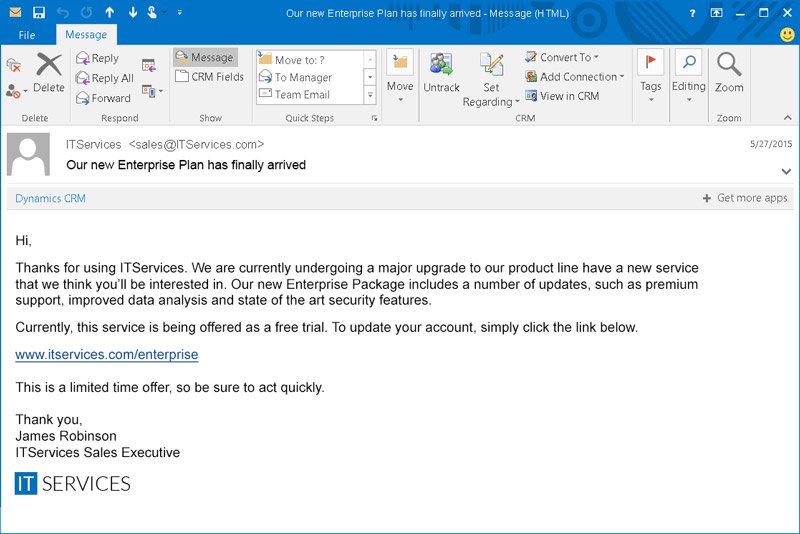
What Is Spear Phishing How Is It Different From Whaling Attacks Imperva

How To Stop Phishing Attacks The Best Tools To Stop Pishing Scams
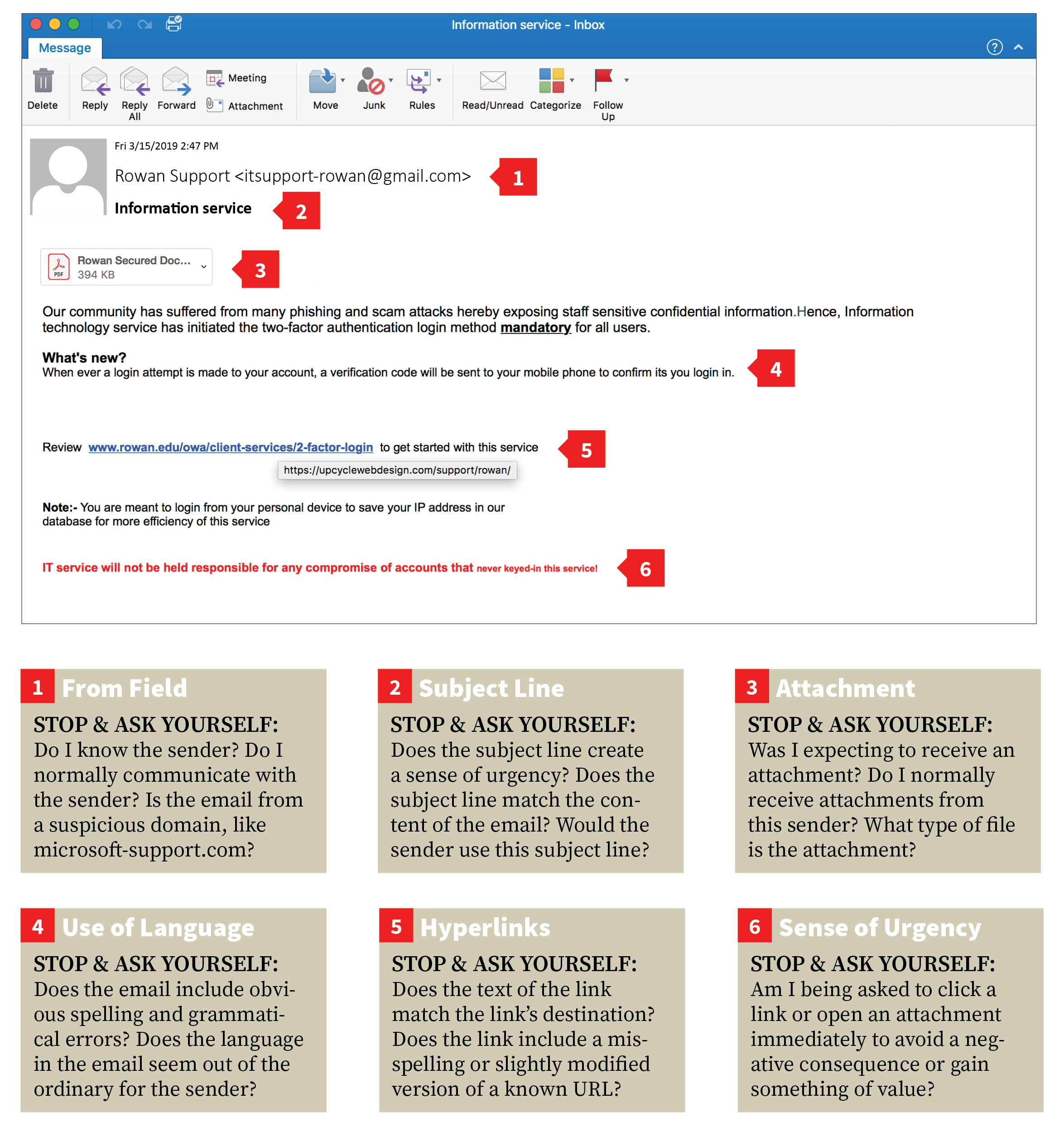
Phishing Other Scams Information Resources And Technology Rowan University

Protecting Students And Faculty From University Phishing Attacks My Techdecisions

Phishing Terminology You Need To Know Metacompliance

Phishing High Res Stock Images Shutterstock

How Phishing Attacks Continue To Exploit Covid 19 Techrepublic

Types Of Phishing Attacks How To Identify Protect In 21

The Rise Of Mobile Phishing Attacks And How To Combat Them Cso Online

You Were Phished What Happens Next Dynasis

How To Identify An Email Phishing Attack Before It S Too Late

Difference Between Phishing And Pharming Fraudwatch International

Filing Your Taxes Watch Out For Phishing Scams Wired

Phishing Knowbe4

3 Reasons You Need To Invest In Anti Phishing Software

4 Sophisticated Phishing Campaigns Impacting The Healthcare Sector

Inside The Modern Phishing Campaigns Of 19 Sonicwall

What To Do If You Fall Victim To A Phishing Scam Xpertechs



